- Home /
- Arcitura Education /
- Certified SOA Security Specialist /
- S90.20 Dumps
Eliminate Risk of Failure with Arcitura Education S90.20 Exam Dumps
Schedule your time wisely to provide yourself sufficient time each day to prepare for the Arcitura Education S90.20 exam. Make time each day to study in a quiet place, as you'll need to thoroughly cover the material for the SOA Security Lab exam. Our actual Certified SOA Security Specialist exam dumps help you in your preparation. Prepare for the Arcitura Education S90.20 exam with our S90.20 dumps every day if you want to succeed on your first try.
All Study Materials
Instant Downloads
24/7 costomer support
Satisfaction Guaranteed
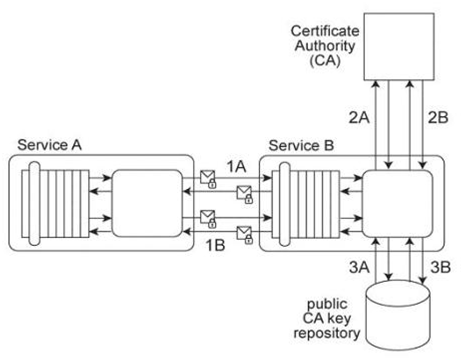
Service A exchanges messages with Service B multiple times during the same runtime service activity. Communication between Services A and B has been secured using transport-layer security. With each service request message sent to Service B (1A .IB), Service A includes an X.509 certificate, signed by an external Certificate Authority (CA). Service B validates the certificate by retrieving the public key of the CA (2A .2B) and verifying the digital signature of the X.509 certificate. Service B then performs a certificate revocation check against a separate external CA repository (3A, 3B). No intermediary service agents reside between Service A and Service B .Service B has recently suffered from poor runtime performance plus it has been the victim of an access-oriented attack. As a result, its security architecture must be changed to fulfill the following new requirements:
1. The performance of security-related processing carried out by Service B when communicating with Service A must be improved.
2. All request messages sent from Service A to Service B must be screened to ensure that they do not contain malicious content. Which of the following statements describes a solution that fulfills these requirements?
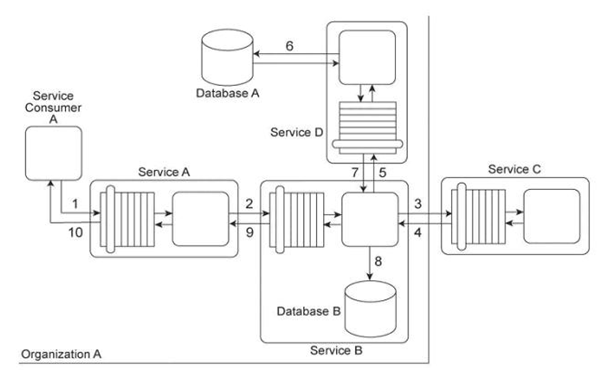
Service Consumer A sends a request message to Service A (1), after which Service A sends a request message to Service B (2). Service B forwards the message to have its contents calculated by Service C (3). After receiving the results of the calculations via a response message from Service C (4), Service B then requests additional data by sending a request message to Service D (5). Service D retrieves the necessary data from Database A (6), formats it into an XML document, and sends the response message containing the XML-formatted data to Service B (7). Service B appends this XML document with the calculation results received from Service C, and then records the entire contents of the XML document into Database B (8). Finally, Service B sends a response message to Service A (9) and Service A sends a response message to Service Consumer A (10). Services A, B and D are agnostic services that belong to Organization A and are also being reused in other service compositions. Service C is a publicly accessible calculation service that resides outside of the organizational boundary. Database A is a shared database used by other systems within Organization A and Database B is dedicated to exclusive access by Service B .Service B has recently been experiencing a large increase in the volume of incoming request messages. It has been determined that most of these request messages were auto-generated and not legitimate. As a result, there is a strong suspicion that the request messages originated from an attacker attempting to carry out denial-of-service attacks on Service B .Additionally, several of the response messages that have been sent to Service A from Service B contained URI references to external XML schemas that would need to be downloaded in order to parse the message data. It has been confirmed that these external URI references originated with data sent to Service B by Service C .The XML parser currently being used by Service A is configured to download any required XML schemas by default. This configuration cannot be changed. What steps can be taken to improve the service composition architecture in order to avoid future denial-of-service attacks against Service B and to further protect Service A from data access-oriented attacks?
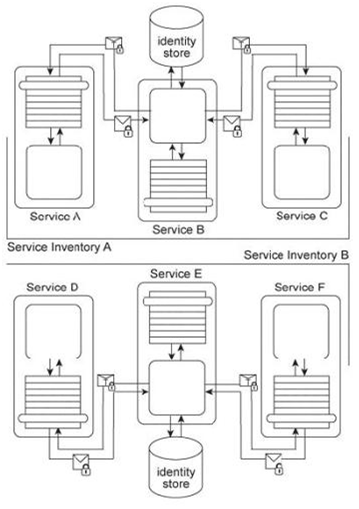
Services A, B, and C reside in Service Inventory A and Services D, E, and F reside in Service Inventory B .Service B is an authentication broker that issues WS-Trust based SAML tokens to Services A and C upon receiving security credentials from Services A and C .Service E is an authentication broker that issues WS-Trust based SAML tokens to Services D and F upon receiving security credentials from Services D and E .Service B uses the Service Inventory A identify store to validate the security credentials of Services A and C .Service E uses the Service Inventory B identity store to validate the security credentials of Services D and F .It is decided to use Service E as the sole authentication broker for all services in Service Inventories A and B .Service B is kept as a secondary authentication broker for load balancing purposes. Specifically, it is to be used for situations where authentication requests are expected to be extra time consuming in order to limit the performance burden on Service E .Even though Service B has all the necessary functionality to fulfill this new responsibility, only Service E can issue SAML tokens to other services. How can these architectures be modified to support these new requirements?
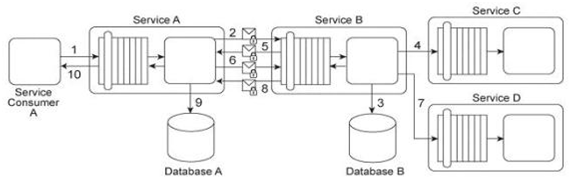
Service Consumer A sends a request message to Service A (1), after which Service A sends a request message with security credentials to Service B (2). Service B authenticates the request and, if the authentication is successful, writes data from the request message into Database B (3). Service B then sends a request message to Service C (4), which is not required to issue a response message. Service B then sends a response message back to Service A (5). After processing Service B's response, Service A sends another request message with security credentials to Service B (6). After successfully authenticating this second request message from Service A, Service B sends a request message to Service D (7). Service D is also not required to issue a response message. Finally, Service B sends a response message to Service A (8), after which Service A records the response message contents in Database A (9) before sending its own response message to Service Consumer A (10). To use Service A, Service Consumer A is charged a per usage fee. The owner of Service Consumer A has filed a complaint with the owner of Service A, stating that the bills that have been issued are for more usage of Service A than Service Consumer A actually used. Additionally, it has been discovered that malicious intermediaries are intercepting and modifying messages being sent from Service B to Services C and D .Because Services C and D do not issue response messages, the resulting errors and problems were not reported back to Service B .Which of the following statements describes a solution that correctly addresses these problems?
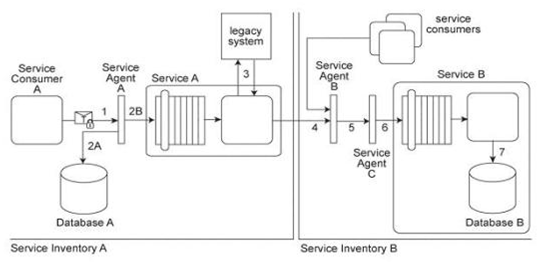
Service Consumer A sends a request message with an authentication token to Service A, but before the message reaches Service A, it is intercepted by Service Agent A (1). Service Agent A validates the security credentials and also validates whether the message is compliant with Security Policy A .If either validation fails, Service Agent A rejects the request message and writes an error log to Database A (2A). If both validations succeed, the request message is sent to Service A (2B). Service A retrieves additional data from a legacy system (3) and then submits a request message to Service B Before arriving at Service B, the request message is intercepted by Service Agent B (4) which validates its compliance with Security Policy SIB then Service Agent C (5) which validates its compliance with Security Policy B .If either of these validations fails, an error message is sent back to Service A .that then forwards it to Service Agent A so that it the error can be logged in Database A (2A). If both validations succeed, the request message is sent to Service B (6). Service B subsequently stores the data from the message in Database B (7). Service A and Service Agent A reside in Service Inventory A .Service B and Service Agents B and C reside in Service Inventory B .Security Policy SIB is used by all services that reside in Service Inventory B .Service B can also be invoked by other service from within Service Inventory B .Request messages sent by these service consumers must also be compliant with Security Policies SIB and B .New services are being planned for Service Inventory A .To accommodate service inventory-wide security requirements, a new security policy (Security Policy SIA) has been created. Compliance to Security Policy SIA will be required by all services within Service Inventory A .Some parts of Security Policy A and Security Policy SIB are redundant with Security Policy SIA .How can the Policy Centralization pattern be correctly applied to Service Inventory A without changing the message exchange requirements of the service composition?
Are You Looking for More Updated and Actual Arcitura Education S90.20 Exam Questions?
If you want a more premium set of actual Arcitura Education S90.20 Exam Questions then you can get them at the most affordable price. Premium Certified SOA Security Specialist exam questions are based on the official syllabus of the Arcitura Education S90.20 exam. They also have a high probability of coming up in the actual SOA Security Lab exam.
You will also get free updates for 90 days with our premium Arcitura Education S90.20 exam. If there is a change in the syllabus of Arcitura Education S90.20 exam our subject matter experts always update it accordingly.
